Safeguard Your Business With 2-Factor Authentication
TechsPlace | Organizations are integrating mobile appointment techniques since they perceive a big prospective to modify their business procedures and enhance relationships with their clients and staff. Though, when including always on-access may abide various organizational advantages and provide an important expediency for users, for organizations it makes more safety risks and chances for information breaks that most companies are easily not safeguarded against.
As organizational technology carries on to grow, safety requirements are being more intricate and various companies cannot safeguard themselves appropriately, making unidentified openings that conciliate information prior a company may do everything regarding it. To make sure mobile is not an expertise creating bigger data breaks, organizations should integrate company-wise safety techniques that may be used cross-ways all inner and outer client-facing interaction use-conditions.
A characteristic corroboration process used on the internet nowadays is single-factor verification, where users provide with a user ID and pass-code. That method has important disadvantages, specifically now that cyber criminals have become more planned and skillful. As per Microsoft, the standard online client includes twenty five accounts, everyone of which needs sign in documentations. On any provided day, an organizational worker may need a six or more pass-codes in a usual path of signing on to Windows, distant admittance, WiFi admittance and e-mail. To ease their individual and working lives, online users way out to making various intricate pass-codes – or not as good as; they employ the similar pass-code or password athwart different sources. The issue is, one time a hacker finds out just a single password, they get admittance to different accounts.
To make matters inferior, online subscribers frequently select the expediency of ‘keep me signed in’ when going through regularly used websites. Most do not understand the innate danger in accomplishing so. The site accumulates a cookie on the system. That cookie may be produced by malware and delivered to an assailant, who may employ it to take off a suitable user and take their online distinctiveness. Various websites also allow users to sign in employing their distinctiveness from social media websites such as LinkedIn and Facebook. Users think that this kind of access is safe as they are not offering a pass-code, when in reality they are easily reusing a current, stationary password and giving a new chance to hackers to break their individual information.
Organizations are taking on mobility since it adds to more output. With cell phone 2FA, staff can steadily see business applications, information, text, and back-office arrangements from almost any tool or place with not keeping the business network and responsive data at jeopardy.
This point of digital ease provides with big possibility for organizations, whereas setting up latest safety perils. Two factor authentication offers the powerful user justification that today’s organizations need, and those not succeeding to use it like an essential portion of their mobile plan are sending-off themselves unwrapped to dreadful outcomes.
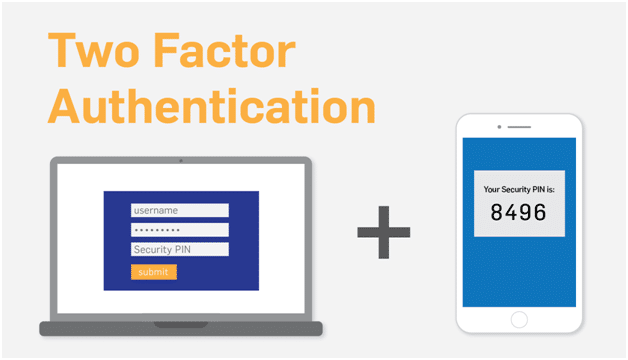
Using Two-Factor Authentication For Effective Mobile Safety
Are pass-codes or passwords deceased? Not completely—but like the single method to sign in, safeguard responsive details, and connection important accounts, user IDs and passwords unaccompanied are no more sufficient. Phishing scams, brute force attacks, data breaks, and SQL inoculation attacks have become common that user IDs and passwords may be simply cracked, detained, and disclosed. On top of that the employment of feeble passwords, similar passwords cross-ways different accounts, and the usage of unsafe WIFI networks, and various people are under the threat of being hacked.
So, how you may safeguard yourself? And, how the applications can we trust on to keep our information safeguarded as well as login procedure?
Two factor authentication has become one of the best methods to make sure the only cause signing into your user account is you, and it is an outstanding method to prevent brute force attacks and lacerates when pass-codes have been cooperated. By needing a second kind of authentication, 2FA is the next stage of safety—and it provides with better serenity of intellect.
It’s quite apparent that simple old pass-codes are an out of date type of safety and not sufficient when we talk about keeping our interactions, accounts, and responsive data safe. Whereas we employ passwords for almost everything—from social accounts and banking to email—many of us still are not employing fundamental best practices for making powerful passwords, or are deteriorating to employ exclusive passwords for every account. It all gets appended to improved susceptibility that’s creating it simpler than always for hackers to filch our pass-codes and details.
2FA administers to create this more complicated by appending a subsequent or second layer of protection. Whereas passwords only give admittance by inquiring something you recognize, 2FA needs both of this and something you contain so as to give access. This signifies whether somebody has obtained your password, till not they are you and involves your phone or different trusted tool into their hand, it would be lot more tricky for them to get admittance to your accounts.
Verification appends a second, frequently physical process to authenticating your individuality, and it is fast being gold customary for safer, more safe logins.
2FA is dependent on offering two of the subsequent three things:
(1) something you recognize, which is your user ID and pass-code grouping.
(2) something you contain, which may be a bank card, smartwatch, mobile phone, or another tool you have marked as secured, and in more highly developed situations.
(3) something you be, which involves bio-metrics such as retina scans, fingerprints, or voice identification.
By needing a user to check their individuality with two or more of these exclusive methods, 2FA is successfully increasing safety further than the password.
In various cases, an exclusive, one-time authentication code is delivered to a tool through an SMS, which you after feed to establish your individuality.
Apart from it, WooCoomerce SMS plugin , Magento SMS gateway, SMS software, etc., are a few important methods that assist effectively in promoting any kind of business.
This article is contributed by guest author on techsplace.com.





